Posts Tagged ‘Data Recovery Tucson’
Is your computer so hopelessly infected with viruses you can’t fix?
Many people ask for help with virus removal when they can not remove the virus because it reinfects as fast as they remove them.
Bit Defender has a bootable rescue cd that you can download and burn with your cd writer sofware.
It is a standard .ISO format.
Boot the cd rom on the infected computer If it’s a dell turn on the pc and press F11 to go to the boot menu and insert the cd rom and choose “Boot from Atapi CD-ROM)
I recommend leaving your computer plugged into the internet for the bitdefender rescue CD to update it’s Virus definitions to get the best results.
(Yes it’s very cool that it boots linux and downloads updates, scans and cleans your computer of viruses)
If you cannot clean an infected file, you may have to delete the file to remove the infection(s).
Again, This is free advice, Use this information in this posting at your own risk. Please don’t blame me if you blow your computer trying to fix your problem.
If this advice helps you remove your virus, please support the good guys like me by clicking the link on your left for bitdefender anti-virus 2009 and purchase a 3 license pack for your family. (Works out to be about $10.00 per computer license.
Not only is this a great value, but it’s also a great anti-virus that will help keep your computer safe.
As always, you can hire me to resolve your virus problem 520-861-1673 as I now offer remote support as well as onsite services.
Antivirus 2009 Malware Removal instructions.
I write this mainly because the Antivirus 2009 is a malware infection that is particularly difficult to remove.
You can’t just uninstall it easily even though there is an uninstaller on the add remove window, it doesn’t work.
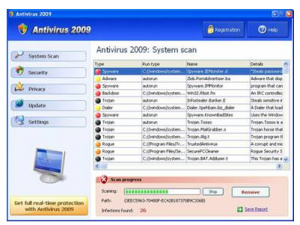
Antivirus 2009 claims to find all kinds of trojans and problems when run and then offers to fix them if you buy the full version. Here’s what it looks like when it is run.
What’s insidious is that this program claims you are infested with all sorts of bad things even if none of them are actually present on your system. What’s for certain is that you should NEVER buy this product, it’s computer extortion.
If you have purchased this antivirus 2009 software to get rid of this stupid thing, call and cancel the charges with your credit card company.
Free tools and advice.
Hijack This is a useful utility for identifying malware and other things that go bump in the night.
Hijack This may have the following registry entries
O2 – BHO: &Research – {037C7B8A-151A-49E6-BAED-CC05FCB50328} – C:\WINDOWS\system32\winsrc.dll
O4 – HKCU\..\Run: [75319611769193918898704537500611] C:\Program Files\Antivirus 2009\av2009.exe
O4 – HKCU\..\Run: [ieupdate] “C:\WINDOWS\system32\ieupdates.exe”
I recommend this method as it is easiest and works well.
Feel free to print out this page before you download and perform the uninstall.
- Download Malware-Bytes malware removal software by clicking on the words in this sentence. Save it to your desktop.
- Close all of your windows down that you can and doubleclick the malware-bytes exe on your desktop.
- take all the default settings and click finish.
- Malware-Bytes will automatically start and ask to update, do so.
- quick scan should be defaulted, click SCAN.
- when the scan is finished, click show results button in the lower right.
- Click remove selected button.
- Your computer should now be freed from the grips of Antivirus 2009
Malware-Bytes is considered one of the next generation of anit-malware technology.
If you like their software, please consider purchasing the full version to defend your computer at the link below:
http://www.malwarebytes.org/mbam.php
For what this is worth, use these instructions at your own risk, don’t blame me if your computer self destructs while it is infected with bugs.
APPENDED:
If you cannot download the latest version, or get this program to install,
Click HERE for a locally hosted version.
I’ve renamed the installer to keep this bug from preventing it’s execution.
Once installed, open my computer, C:, Program files,Malware Bytes.
Right click mbam.exe and copy
Right click and paste.
You will see a new file called copy of mbam.exe appear,
Execute this version as it will run where the other version has been blocked by antivirus 2009.
In addition:
Please download gmer here (renamed to cmer.exe) and excecute it to be certain you are not infected with a rootkit. If you find yourself infected, please call me immediately.
Thank you.
520-861-1673
Chuck House
My criteria for selecting a data recovery specialist
- How much experience do their technicians have? (I have 20 years)
- What is their success rate? (mine is about 75%) anyone who claims over 80% is simply lying about theirs.
- Do they have a clean room? a clean bench? can they change heads? Transfer platters? (all these services are expensive but we can do them.)
- Do they offer references and do you know/trust them? I rely on referrals to bring me business.
- Do they offer to help you setup better backup systems? An ounce of prevention is …
- You only get one attempt at this recovery – so make the best of it and give us a call.
Ten ways to avoid needing to use data recovery services.
- Backup, Backup, Backup. Use a good offsite backup service and maintain good onsite backups. I have been recommending iBackup to my clients for a couple of years now and have been pleased with ease of use and performance.
- If you hear funny noises, shut down your computer and have it looked at immediately. Clicking and chattering are not normal.
- Use a good anti-virus software and anti-spyware software. These help cut down on software damaged drives. See my Discounts page for some of the software options I recommend, or email me for specific recommendations for your situation.
- Purchase and maintain a good UPS (Uninterruptible Power Supply). This is important because about 30% of the drives we see are electronically damaged in brown-outs.
- Clean the inside of your computer out (canned air is a wonderful thing!) and change the power-supply once every year. (Especially servers.) Maintenance is a good way to avoid damage. Dust seals in the heat and keeps the air from getting to the aluminum to wick off the heat. Aluminum radiates less than 2% of its energy so air/metal contact is a must. Clean more frequently if you work in a dusty environment.
- On critical systems, implement a RAID architecture. Mirroring or RAID 5 or more is preferred. This means it takes more than one drive failing to cause a crash.
- Restore your backups on a semi-annual basis to check that your backups are complete.
- Do not, under any circumstances, while running or not, shake or hit the drive. This can lead to irreparable damage. This would seem like something I don’t have to tell you, but you’d be surprised how many people use the old “kick it and see if that fixes it” mentality.
- Do not have food around your computer, particularly laptops. Sodas are the number one reason laptops seem to die (At least the ones sent to me)
- Finally, do not immerse in water. Water will destroy your drive. Why? Hard disks are exposed to the air so they can properly maintain a pressure inside the drive. Water will seep inside the drive and corrode the surface.